IN THIS SECTION
CFPB Report: 2013-IT-C-020 December 2, 2013
2013 Audit of the CFPB's Information Security Program
available formats
-
Executive Summary:
PDF | HTML -
Full Report:
PDF (3 MB) | HTML
Analysis of the CFPB's Progress in Implementing Key FISMA and DHS Information Security Program Requirements
Continuous Monitoring
Requirement
FISMA requires agencies to perform periodic testing and evaluation of the effectiveness of their information security policies, procedures, and practices. To implement this requirement, guidance issued by the National Institute of Standards and Technology (NIST) and the DHS focuses on the process of information security continuous monitoring (ISCM). Specifically, ISCM is the process of maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk-management decisions. The key components of an ISCM program are outlined in NIST Special Publication 800-137, Information Security Continuous Monitoring for Federal Information Systems and Organizations (SP 800-137) and highlighted in figure 1.
Figure 1: Components of an ISCM Program
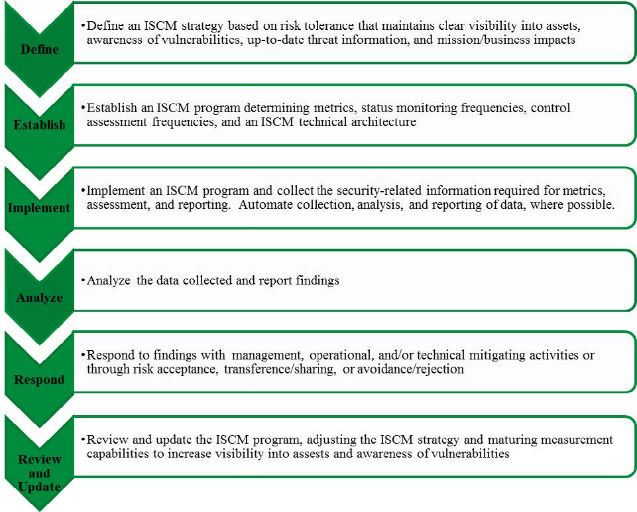
Source: Office of Inspector General analysis of NIST SP 800-137.
Progress to Date
The CFPB has taken several steps to develop and implement an ISCM program that is consistent with SP 800-137. For instance, the CFPB has developed policies, procedures, and an overall strategy for continuous monitoring. The CFPB's continuous monitoring strategy defines a process for ongoing security controls assessment, including identifying the security controls to be tested and the interval for assessment. The strategy also highlights the importance of vulnerability scanning in ensuring the protection of CFPB systems and data, and outlines frequencies for infrastructure, operating system, database, and application-level vulnerability scanning. In support of the continuous monitoring strategy, the CFPB has implemented change control processes and tools to track and analyze the security impact of changes. The CFPB is also utilizing an automated tool to perform weekly vulnerability scanning of the agency's operating systems and network devices.
Work to Be Done
We found that additional actions are needed to fully establish and implement CFPB's continuous monitoring strategy. Specifically, the CFPB has not defined metrics to facilitate decisionmaking and improve performance of its ISCM. NIST guidance notes that metrics can increase accountability, improve effectiveness of information security activities, and provide information for resource allocation decisions. We also noted opportunities to strengthen the CFPB's ISCM program through use of additional automated tools to more comprehensively assess security controls and system configurations. For instance, while the CFPB utilizes an automated tool to perform vulnerability assessments at the operating system and network levels, it does not have such tools to assess database and application-level vulnerabilities.
The CFPB finalized its continuous monitoring strategy in July 2013, and CFPB officials informed us that full implementation of the strategy is not expected until April 2014. Performance measures and automated tools to comprehensively assess security controls and system configurations will help the CFPB effectively identify information security weaknesses and manage all risks facing the organization.
Recommendation
We recommend that the CIO
-
Strengthen the CFPB's ISCM program by
- defining and implementing performance measures to facilitate decisionmaking and improve performance of the agency's continuous monitoring program.
- identifying additional automated tools to assess security controls and analyze and respond to the results of continuous monitoring activities.
Management's Response
The CIO concurred with our recommendation and noted that the CFPB is pursuing the use of additional automated tools and an improved use of performance measures to enhance its continuous monitoring program.
OIG Comment
In our opinion, the actions described by the CIO are responsive to our recommendation. We plan to follow up on the actions to ensure that the recommendation is fully addressed.
Configuration Management
Requirement
Configuration management refers to a collection of activities focused on establishing and maintaining the integrity of products and systems through control of the processes for initializing, changing, and monitoring their configurations. From an information security perspective, configuration management refers to the management and control of secure configurations for an information system in accordance with organizational security requirements. FISMA requires agencies to develop and ensure compliance with minimally acceptable security configurations. Best practices for security-focused configuration management programs are outlined in NIST Special Publication 800-128, Guide for Security-Focused Configuration Management of Information Systems (SP 800-128). SP 800-128 notes that federal agencies should develop and implement common, secure configuration settings for information systems and a robust patch management process to reduce vulnerabilities. SP 800-128 further states that agencies should develop a configuration management plan to describe how these processes will be managed across the organization.
Progress to Date
The CFPB has implemented components of an overall configuration management program. For instance, the CFPB has developed secure configuration settings and multiple security engineering baselines for technologies utilized at the agency. The CFPB has also implemented processes and an automated tool to manage information system changes and ensure that security impacts to configuration baselines are assessed and approved.
Work to Be Done
We found that the CFPB has not developed and implemented an organization-wide configuration management plan and a consistent process for patch management. A configuration management plan would provide a comprehensive description of the roles, responsibilities, policies, and procedures that apply when managing the configuration of information systems. CFPB officials notified us that such a plan had not been developed, because the agency was focused on achieving operational capabilities and establishing its information technology infrastructure, as it transitioned away from Treasury. In a 2013 security control review of a CFPB system, we found that security patches for this system had not been installed in a timely manner and system devices were not securely configured in accordance with the CFPB's baseline configurations. An organization-wide configuration management plan can help ensure that CFPB systems are patched in a timely manner and securely configured.
Recommendation
We recommend that the CIO
- Develop and implement an organization-wide configuration management plan and a consistent process for patch management.
Management's Response
The CIO concurred with our recommendation and noted that configuration management is a priority area for maturing CFPB's enterprise architecture in the coming year. In addition, the CIO noted that the CFPB plans to centralize the implementation of patch management.
OIG Comment
In our opinion, the actions described by the CIO are responsive to our recommendation. We plan to follow up on the actions to ensure that the recommendation is fully addressed.
Security Training
Requirement
FISMA requires agencies to provide security awareness training to all information system users to inform them of risks associated with their activities and their responsibilities in complying with security policies and procedures. FISMA also requires agencies to provide role-based training to individuals with significant security responsibilities. The primary difference between security awareness training and role-based training is that the former is geared toward focusing all users on overall information security policies, while the latter is geared toward teaching information security skills needed to perform specific information technology functions. Best practices for developing and implementing a security training program are outlined in NIST Special Publication 800-50, Building an Information Technology Security Awareness and Training Program (SP 800-50). SP 800-50 highlights the important role that training plays in ensuring the effective implementation of an agency's information security program and notes that individuals with significant security responsibilities include system and network administrators, managers, and security officers. SP 800-50 also identifies four critical steps in the life cycle of an information technology security awareness and training program. These steps are program design, development, implementation, and post-implementation.
Progress to Date
The CFPB has developed and implemented security awareness training that is required to be completed by all employees and contractors on an annual basis. Our review of the content of the CFPB's security awareness training found that it included topics recommended in SP 800-50 and other best practices. In addition, the CFPB conducts information security awareness training sessions every two weeks, provides security awareness training in new hire briefings, and provides ongoing security awareness updates on the agency's intranet site and other internal mediums.
Work to Be Done
The CFPB has not designed, developed, and implemented a role-based training program for individuals with significant security responsibilities. We attribute this to the recent finalization of key CFPB policies and procedures that outline roles and responsibilities for individuals with significant security responsibilities. Further, in 2013, the CFPB focused on transitioning security awareness services from Treasury before establishing a role-based security training program. A role-based security training program will help provide the CFPB with assurance that employees and contractor staff with significant security responsibilities have adequate knowledge and expertise to ensure the effective and efficient implementation of the agency's information security program.
Recommendation
We recommend that the CIO
- Design, develop, and implement a role-based security training program for individuals with significant security responsibilities.
Management's Response
The CIO concurred with our recommendation and noted that the CFPB plans to finalize its current role-based security training strategy and ensure that individuals with significant security responsibilities receive appropriate training.
OIG Comment
In our opinion, the actions described by the CIO are responsive to our recommendation. We plan to follow up on the actions to ensure that the recommendation is fully addressed.
Incident Response and Reporting
Requirement
FISMA requires agencies to develop and implement procedures for detecting, reporting, and responding to security incidents, including mitigating risks of such incidents before substantial damage is done. Best practices for establishing incident detection, reporting, and response capabilities are outlined in NIST Special Publication 800-61, Revision 1, Computer Security Incident Handling Guide (SP 800-61). SP 800-61 states that agencies should create an incident response policy, plan, and procedures. Further, given the multitude of sources and signs of incident activity occurring in organizations' information systems, SP 800-61 emphasizes the importance of using automated correlation and centralized logging tools to analyze incident data. Correlating events among multiple indicator sources can be valuable in detecting whether a particular incident occurred as well as in mitigating risks before substantial damage is done.
Progress to Date
The CFPB has taken several steps to develop a capability to detect, report, and respond to security incidents. For example, the CFPB has developed an organization-wide incident response policy and plan that defines the processes and roles and responsibilities for computer incident response activities at the CFPB, including for third-party providers. The CFPB has also established a computer security incident response team and developed a centralized tracking tool for documenting, monitoring, and ensuring adequate response to incidents. Further, the CFPB is in the process of building a tool to collect audit logging and incident data from various systems to support the detection, validation, and correlation of incidents.
Work to Be Done
We found that the CFPB had not fully implemented a capability to correlate information on incident activity. Specifically, the tool used by the CFPB to collect audit logging and incident data across CFPB systems does not yet include data from all relevant sources, including some third-party systems. For a select system that we reviewed, we noted that while a variety of audit and incident logs were being generated by system devices, they were not being centrally analyzed or correlated for anomalous activity. Weaknesses in CFPB's capability to comprehensively correlate events among multiple indicator sources are a result of the developing maturity of the CFPB's incident management program. Specifically, agency officials have prioritized establishing the policies, procedures, and overall structure of the CFPB's incident response capability. Centrally analyzed and correlated information on incident activity will help ensure that the CFPB can fully detect and respond to information security incidents in a timely manner.
Recommendation
We recommend that the CIO
- Ensure that audit logs and security incident information from all relevant sources are centrally tracked, analyzed, and correlated.
Management's Response
The CIO concurred with our recommendation and noted that the CFPB plans to further automate the collection, correlation, and reporting of audit logs and security incident information in fiscal year 2014.
OIG Comment
In our opinion, the actions described by the CIO are responsive to our recommendation, and we plan to follow up on the actions to ensure that the recommendation is fully addressed.
